[Day 6] Email Analysis It’s beginning to look a lot like phishing¶
Elf McBlue found an email activity while analysing the log files. It looks like everything started with an email…
IMPORTANT NOTES:
Given email sample contains a malicious attachment.
Never directly interact with unknown email attachments outside of an isolated environment.
Le cours¶
Learning Objectives¶
Learn what email analysis is and why it still matters.
Learn the email header sections.
Learn the essential questions to ask in email analysis.
Learn how to use email header sections to evaluate an email.
Learn to use additional tools to discover email attachments and conduct further analysis.
Help the Elf team investigate the suspicious email received.
What is Email Analysis?¶
Email analysis is the process of extracting the email header information to expose the email file details. The email header contains the technical details of the email like sender, recipient, path, return address and attachments. Usually, these details are enough to determine if there is something suspicious/abnormal in the email and decide on further actions on the email, like filtering/quarantining or delivering. This process can be done manually and with the help of tools.
There are two main concerns in email analysis.
Security issues: Identifying suspicious/abnormal/malicious patterns in emails.
Performance issues: Identifying delivery and delay issues in emails.
In this task, we will focus on security concerns on emails, a.k.a. phishing. Before focusing on the hands-on email analysis, you will need to be familiar with the terms « social engineering » and « phishing ».
Social engineering: Social engineering is the psychological manipulation of people into performing or divulging information by exploiting weaknesses in human nature. These « weaknesses » can be curiosity, jealousy, greed, kindness, and willingness to help someone.
Phishing: Phishing is a sub-section of social engineering delivered through email to trick someone into either revealing personal information and credentials or executing malicious code on their computer.
Phishing emails will usually appear to come from a trusted source, whether that’s a person or a business. They include content that tries to tempt or trick people into downloading software, opening attachments, or following links to a bogus website. You can find more information on phishing by completing the phishing module.
Does the Email Analysis Still Matter?¶
Yes! Various academic research and technical reports highlight that phishing attacks are still extremely common, effective and difficult to detect. It is also part of penetration testing and red teaming implementations (paid security assessments that examine organisational cybersecurity). Therefore, email analysis competency is still an important skill to have. Today, various tools and technologies ease and speed up email analysis. Still, a skilled analyst should know how to conduct a manual analysis when there is no budget for automated solutions. It is also a good skill for individuals and non-security/IT people!
Important Note: In-depth analysis requires an isolated environment to work. It is only suggested to download and upload the received emails and attachments if you are in the authorised team and have an isolated environment. Suppose you are outside the corresponding team or a regular user. In that case, you can evaluate the email header using the raw format and conduct the essential checks like the sender, recipient, spam score and server information. Remember that you have to inform the corresponding team afterwards.
How to Analyse Emails?¶
Before learning how to conduct an email analysis, you need to know the structure of an email header. Let’s quickly review the email header structure.
Field |
Details |
|---|---|
From |
The sender’s address. |
To |
The receiver’s address, including CC and BCC. |
Date |
Timestamp, when the email was sent. |
Subject |
The subject of the email. |
Return Path |
The return address of the reply, a.k.a. « Reply-To ». If you reply to an email, the reply will go to the address mentioned in this field. |
Domain Key and DKIM Signatures |
Email signatures are provided by email services to identify and authenticate emails. |
SPF |
Shows the server that was used to send the email.It will help to understand if the actual server is used to send the email from a specific domain. |
Message-ID |
Unique ID of the email. |
MIME-Version |
Used MIME version.It will help to understand the delivered « non-text » contents and attachments. |
X-Headers |
The receiver mail providers usually add these fields.Provided info is usually experimental and can be different according to the mail provider. |
X-Received |
Mail servers that the email went through. |
X-Spam Status |
Spam score of the email. |
X-Mailer |
Email client name. |
Important Email Header Fields for Quick Analysis¶
Analysing multiple header fields can be confusing at first glance, but starting from the key points will make the analysis process slightly easier. A simple process of email analysis is shown below.
Questions to Ask / Required Checks |
Evaluation |
|---|---|
Do the « From », « To », and « CC » fields contain valid addresses? |
Having invalid addresses is a red flag. |
Do the « From » and « To » fields are the same? |
Having the same sender and recipient is a red flag. |
Do the « From » and « Return-Path » fields are the same? |
Having different values in these sections is a red flag. |
Was the email sent from the correct server? |
Email should have come from the official mail servers of the sender. |
Does the « Message-ID » field exist, and is it valid? |
Empty and malformed values are red flags. |
Do the hyperlinks redirect to suspicious/abnormal sites? |
Suspicious links and redirections are red flags. |
Do the attachments consist of or contain malware? |
Suspicious attachments are a red flag. File hashes marked as suspicious/malicious by sandboxes are a red flag. |
Text editors are helpful in analysis, but there are some tools that can help you to view the email details in a clearer format. In this task, we will use the « emlAnalyzer » tool to view the body of the email and analyse the attachments. The emlAnalyzer is a tool designed to parse email headers for a better view and analysis process. The tool is ready to use in the given VM. The tool can show the headers, body, embedded URLs, plaintext and HTML data, and attachments.
Additionally, you can use some Open Source Intelligence (OSINT) tools to check email reputation and enrich the findings. Visit the given site below and do a reputation check on the sender address and the address found in the return path.
Email reputation check¶
Tool: https://emailrep.io/
Here, if you find any suspicious URLs and IP addresses, consider using some OSINT tools for further investigation. While we will focus on using Virustotal and InQuest, having similar and alternative services in the analyst toolbox is worthwhile and advantageous.
Tool |
Purpose |
|---|---|
VirusTotal |
A service that provides a cloud-based detection toolset and sandbox environment. |
InQuest |
A service provides network and file analysis by using threat analytics. |
IPinfo .io |
A service that provides detailed information about an IP address by focusing on geolocation data and service provider. |
Talos Reputation |
An IP reputation check service is provided by Cisco Talos. |
Urlscan .io |
A service that analyses websites by simulating regular user behaviour. |
Browserling |
A browser sandbox is used to test suspicious/malicious links. |
Wannabrowser |
A browser sandbox is used to test suspicious/malicious links. |
After completing the mentioned initial checks, you can continue with body and attachment analysis. Now, let’s focus on analysing the email body and attachments. The sample doesn’t have URLs, only an attachment. You need to compute the value of the file to conduct file-based reputation checks and further your analysis. As shown below, you can use the sha256sum tool/utility to calculate the file’s hash value.
Les questions :¶
Avant les questions, regardons le mail en question :
X-Pm-Content-Encryption: end-to-end
X-Pm-Origin: internal
Subject: Urgent: Blue section is down. Switch to the load share plan!
From: Chief Elf <chief.elf@santaclaus.thm>
Date: Tue, 6 Dec 2022 00:00:01 +0000
Mime-Version: 1.0
Content-Type: multipart/mixed;boundary=---------------------03edd9c682a0c8f60d54b9e4bb86659f
To: elves.all@santaclaus.thm <elves.all@santaclaus.thm>
X-Attached: Division_of_labour-Load_share_plan.doc
Message-Id: <QW9DMjAyMl9FbWFpbF9BbmFseXNpcw==>
X-Pm-Spamscore: 3
Received: from mail.santaclaus.thm by mail.santaclaus.thm; Tue, 6 Dec 2022 00:00:01 +0000
X-Original-To: elves.all@santaclaus.thm
Return-Path: <murphy.evident@bandityeti.thm>
Delivered-To: elves.all@santaclaus.thm
-----------------------03edd9c682a0c8f60d54b9e4bb86659f
Content-Type: multipart/related;boundary=---------------------8f117c48beda7f1c1da0a5a894d5c4b5
-----------------------8f117c48beda7f1c1da0a5a894d5c4b5
Content-Type: text/html;charset=utf-8
Content-Transfer-Encoding: base64
[...]
Content-Type: application/msword; filename="Division_of_labour-Load_share_plan.doc"; name="Division_of_labour-Load_share_plan.doc"
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename="Division_of_labour-Load_share_plan.doc"; name="Division_of_labour-Load_share_plan.doc"
Question 1 : What is the email address of the sender?¶
En regardant le mail, on voit bien la ligne : From: Chief Elf <chief.elf@santaclaus.thm>
Question 2 : What is the return address?¶
Idem ici, ça reste relativement simple : Return-Path: <murphy.evident@bandityeti.thm>
Question 3 : On whose behalf was the email sent?¶
Il s’agit de dire quel est l’expédieur ==> Chief Elf
Question 4 : What is the X-spam score?¶
Le score de spam se trouve ici X-Pm-Spamscore: 3. Plus t’es bas, plus ça pue, en dessous de 7, c’est souvent considéré comme du spam. Mes mails sont à 10(/10 :sunglass:).
Question 6 : Visit the email reputation check website provided in the task. What is the reputation result of the sender’s email address?¶
Un petit tour sur l’outil mis plus haut, on entre l’email et on apprends que cette dernière est RISKY
Question 7 : Check the attachments. What is the filename of the attachment?¶
Encore une fois, tout est dans le mail. Content-Disposition: attachment; filename="Division_of_labour-Load_share_plan.doc"; name="Division_of_labour-Load_share_plan.doc"
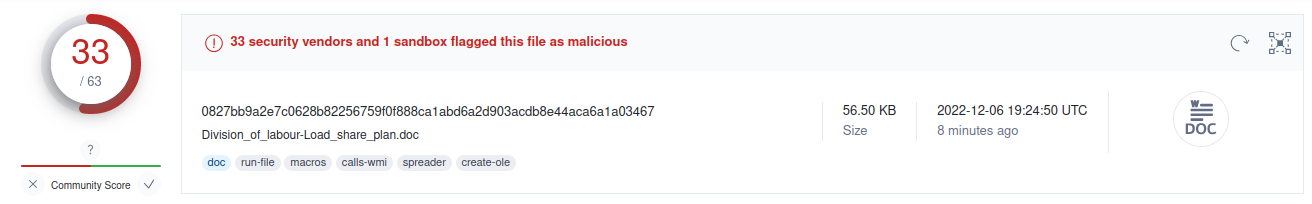
Question 8 : What is the hash value of the attachment?¶
Pour ça, il faut tout d’abord récupérer le fichier doc.
ubuntu@ip-10-10-232-102:~$ emlAnalyzer -i ./Desktop/Urgent\:.eml --extract-all
[+] Attachment [1] "Division_of_labour-Load_share_plan.doc" extracted to eml_attachments/Division_of_labour-Load_share_plan.doc
ubuntu@ip-10-10-232-102:~$ sha256sum eml_attachments/Division_of_labour-Load_share_plan.doc
0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a03467 eml_attachments/Division_of_labour-Load_share_plan.doc
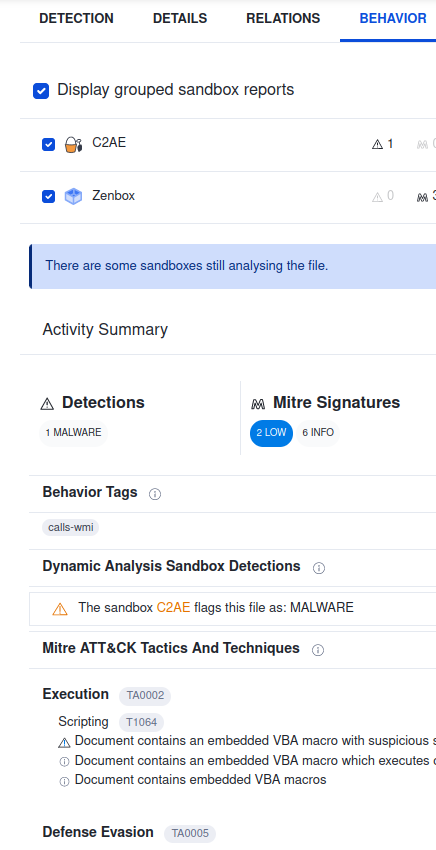
Question 10 : Visit the InQuest website and use the hash value to search. What is the subcategory of the file?¶
On réitère la même requête sur Inquest Labs et l’on trouve un macro_hunter.